4D v16
Encrypting Client/Server Connections
- 4D Server Reference
-
- Using 4D Server
-
- Creating a New 4D Server Database
- Exiting 4D Server
- Using 4D Server 64-bit version (Windows)
- Using 4D Server 64-bit version (OS X)
- 4D Server Menus
- Network and Client-Server options
- IP Configuration
- Encrypting Client/Server Connections
- Single Sign On (SSO) on Windows
- Managing the Resources folder
- Registering a Database as a Service
- Setting up a logical mirror
 Encrypting Client/Server Connections
Encrypting Client/Server Connections
You can configure the client/server connections so that 4D Server and 4D remote workstations communicate in secured mode. The secured client/server communication is based on TLS (Transport Layer Security) protocol, which was formerly the SSL (Secured Socket Layer).
Note: For a general overview of 4D's security features, see the 4D Security guide.
The TLS protocol has been designed to secure data exchanges between two applications —primarily between a Web server and a browser. It is designed to authenticate the sender and receiver, and to guarantee the confidentiality and integrity of the exchanged information. For a detailed description of the secured protocol, refer to section Using TLS Protocol in the 4D Language Reference.
Between 4D Server and a remote 4D, authentication and integrity mechanisms are handled transparently by 4D Server and do not require any additional user setting.
Note: Encrypting client/server connections slows connections.
At the network level, the TLS protocol is inserted between the TCP/IP layer (low level) and the high level protocol.
To use TLS in a “classic” client/server architecture, the following certificate files must be present:
- key.pem: document containing private encryption key
- cert.pem: document containing certificate.
These files must be located in the Resources subfolder of the 4D Server and 4D applications. They must be present on the server machine and on each remote machine. Default key.pem and cert.pem files are provided with 4D. For a higher level of security, we strongly recommend that you replace these files with your own certificates. For more information about creating custom certificates, refer to the How to get a certificate? section of 4D's Web server documentation (the procedure is identical).
You must also enable connections in secured mode.
To do this, open the “Client-Server/Network options” page of the Database settings dialog box and select the option Encrypt Client/Server Connections in the “Encryption” area (see the Network and Client-Server options section).
By default, the option is not checked.
You must then quit and relaunch 4D Server so that this setting is taken into account.
All 4D remote stations will then connect in secured mode.
- Use of ServerNet
When the new ServerNet network layer is used, the activation of the secured protocol on the server is transparent (the publication mode does not appear in the connection dialog box). The connection and switch to secure mode takes place following an internal negotiation between the server application and the remote application.
For more information about the ServerNet, refer to the Network and Client-Server options section.
- Use of legacy network layer
When the legacy network layer is used, the “circumflex accent” (^) is placed before the name of the databases published in TLS mode in the TCP/IP page of the connection dialog box in 4D Server:
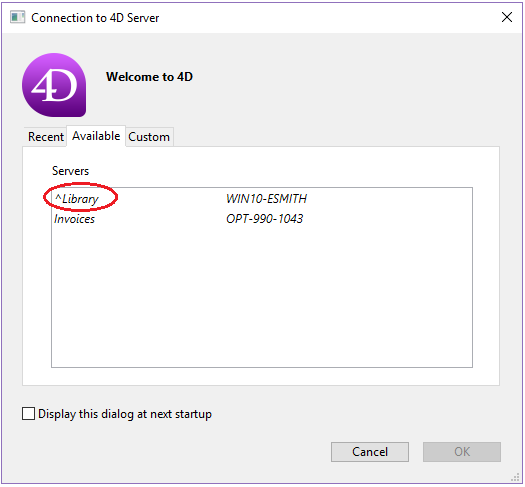
Note:When a database is not published dynamically on the TCP/IP page of the Connection dialog box, the user can enter its name in the Custom page (see the Connecting to a 4D Server Database and IP Configuration sections). In this case, a ^ (circumflex accent) must be placed before the database name if the database is published in secured mode; otherwise the connection will be rejected .
Product: 4D
Theme: Using 4D Server
4D Server Reference ( 4D v16)









