4D v14.3
ENCRYPT BLOB
- 4D Language Reference
-
- BLOB
-
- BLOB Commands
- BLOB PROPERTIES
- BLOB size
- BLOB TO DOCUMENT
- BLOB to integer
- BLOB to list
- BLOB to longint
- BLOB to real
- BLOB to text
- BLOB TO VARIABLEUpd
- COMPRESS BLOB
- COPY BLOB
- DECRYPT BLOB
- DELETE FROM BLOB
- DOCUMENT TO BLOB
- ENCRYPT BLOB
- EXPAND BLOB
- INSERT IN BLOB
- INTEGER TO BLOB
- LIST TO BLOB
- LONGINT TO BLOB
- REAL TO BLOB
- SET BLOB SIZE
- TEXT TO BLOB
- VARIABLE TO BLOBUpd
 ENCRYPT BLOB
ENCRYPT BLOB
| ENCRYPT BLOB ( toEncrypt ; sendPrivKey {; recipPubKey} ) | ||||||||
| Parameter | Type | Description | ||||||
| toEncrypt | BLOB |

|
Data to encrypt | |||||

|
Encrypted data | |||||||
| sendPrivKey | BLOB |

|
Sender’s private key | |||||
| recipPubKey | BLOB |

|
Recipient’s public key | |||||
The ENCRYPT BLOB command encrypts the content of the toEncrypt BLOB with the sender’s private key sendPrivKey, as well as optionally the recipient’s public key recipPubKey. These keys should be generated by the command GENERATE ENCRYPTION KEYPAIR (within the “Secured Protocol” theme).
Note: This command uses the SSL protocol algorithm and encryption features. To be able to use this command, make sure that the components necessary to the SSL protocol are installed properly on your machine — even though you do not want to use SSL for 4D Web server connections. For detailed information on this protocol, please refer to section Using SSL Protocol.
- If one key is used for the encryption (the sender’s private key), only people in possession of the public key will be able to read the information. This system guarantees that the sender himself has encrypted the information.
- The simultaneous use of the sender’s private key and recipient’s public key guarantees that only one recipient will be able to read the information.
The BLOB containing the keys has a PKCS internal format. This standard cross platform format allows exchanging or handling keys simply by copy-pasting in an Email or a text file.
Once the command has been run, the toEncrypt BLOB contains the encrypted data that will be decrypted only with the DECRYPT BLOB command, with the sender’s public key passed as parameter.
Moreover, if the optional recipient’s public key has been used to encrypt the information, the recipient’s private key will also be necessary for decrypting.
Encryption principle with public and private keys for message exchange between two people, “Alice” and “Bob”:
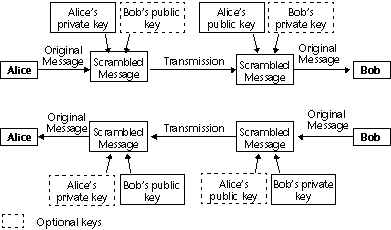
Note: The cipher contains a checksum functionality in order to avoid any BLOB content modification (deliberately or not). Consequently, an encrypted BLOB should not be modified otherwise it might not be decrypted.
Data encryption slows down the execution of your applications, especially if a pair of keys is used. However, you can consider the following optimization tips:
- Depending on the current available memory, the command will execute in “synchronous” or “asynchronous” mode.
The asynchronous mode is faster, since it does not freeze the other processes. This mode is automatically used if the available memory is at least twice the size of the data to encrypt.
Otherwise, for security reasons, the synchronous mode is used. This mode is slower since it freezes the other processes. - Regarding large BLOBs, you can encrypt only a small “strategic” part of the BLOB in order to reduce the size of data to be processed as well as the processing time.
- Using a single key
1) The company generates a pair of keys with the command GENERATE ENCRYPTION KEYPAIR:
`Method GENERATE_KEYS_TXT
C_BLOB($BPublicKey;$BPrivateKey)
GENERATE ENCRYPTION KEYPAIR($BPrivateKey;$BPublicKey)
BLOB TO DOCUMENT("PublicKey.txt";$BPublicKey)
BLOB TO DOCUMENT("PrivateKey.txt";$BPrivateKey)2) The company keeps the private key and sends a copy of the document containing the public key to each subsidiary. For maximum security, the key should be copied on a disk handed over to the subsidiaries.
3) Then the company copies the private information (stored in the text field, for example) in BLOBs which will be encrypted with the private key:
`Method ENCRYPT_INFO
C_BLOB($vbEncrypted;$vbPrivateKey)
C_TEXT($vtEncrypted)
$vtEncrypted:=[Private]Info
VARIABLE TO BLOB($vtEncrypted;$vbEncrypted)
DOCUMENT TO BLOB("PrivateKey.txt";$vbPrivateKey)
If(OK=1)
ENCRYPT BLOB($vbEncrypted;$vbPrivateKey)
BLOB TO DOCUMENT("Update.txt";$vbEncrypted)
End if4) The update files can be sent to the subsidiaries (though a non-secured channel such as the Internet). If a third person gets hold of the encrypted file, he will not be able to decrypt it without the public key.
5) Each subsidiary can decrypt the document with the public key:
`Method DECRYPT_INFO
C_BLOB($vbEncrypted;$vbPublicKey)
C_TEXT($vtDecrytped)
C_TIME($vtDocRef)
ALERT("Please select an encrypted document.")
$vtDocRef:=Open document("") `Select Update.txt
If(OK=1)
CLOSE DOCUMENT($vtDocRef)
DOCUMENT TO BLOB(Document;$vbEncrypted)
DOCUMENT TO BLOB("PublicKey.txt";$vbPublicKey)
If(OK=1)
DECRYPT BLOB($vbEncrypted;$vbPublicKey)
BLOB TO VARIABLE($vbEncrypted;$vtDecrypted)
CREATE RECORD([Private])
[Private]Info:=$vtDecrypted
SAVE RECORD([Private])
End if
End if- Using keypairs
A company wants to use the Internet to exchange information. Each subsidiary receives private information and also sends information to the corporate office. Consequently there are two requirements:
- The recipient only should be able to read the message,
- The recipient must have proof that the message was sent by the sender himself.
1) The corporate office and each subsidiary generate their own key pairs (with the GENERATE_KEYS_TXT method).
2) The private key is kept secret by both sides. Each subsidiary sends its public key to the corporate office who, in its turn, sends its public key too. This key transfer does not need to be done through a secured channel as the public key is not enough to decrypt the message.
3) To encrypt the information to send, the subsidiary or the corporate house executes the ENCRYPT_INFO_2 method which uses the sender’s private key and the recipient’s public key to encrypt the information:
`Method ENCRYPT_INFO_2
C_BLOB($vbEncrypted;$vbPrivateKey;$vbPublicKey)
C_TEXT($vtEncrypt)
C_TIME($vtDocRef)
$vtEncrypt:=[Private]Info
VARIABLE TO BLOB($vtEncrypt;$vbEncrypted)
` Your own private key is loaded...
DOCUMENT TO BLOB("PrivateKey.txt";$vbPrivateKey)
If(OK=1)
` ...and the recipient’s public key
ALERT("Please select the recipient’s public key.")
$vhDocRef:=Open document("") `Public key to load
If(OK=1)
CLOSE DOCUMENT($vtDocRef)
DOCUMENT TO BLOB(Document;$vbPublicKey)
`BLOB encryption with the two keys as parameters
ENCRYPT BLOB($vbEncrypted;$vbPrivateKey;$vbPublicKey)
BLOB TO DOCUMENT("Update.txt";$vbEncrypted)
End if
End if4) The encrypted file can then be sent to the recipient via the Internet. If a third person gets hold of it, he or she will not be able to decrypt the message, even if he or she has the public keys as the recipient’s private key will also be required.
5) Each recipient can decrypt the document by using his/her own private key and the sender’s public key:
`Method DECRYPT_INFO_2
C_BLOB($vbEncrypted;$vbPublicKey;$vbPrivateKey)
C_TEXT($vtDecrypted)
C_TIME($vhDocRef)
ALERT("Please select the encrypted document.")
$vhDocRef:=Open document("") `Select the Update.txt file
If(OK=1)
CLOSE DOCUMENT($vhDocRef)
DOCUMENT TO BLOB(Document;$vbEncrypted)
`Your own private key is loaded
DOCUMENT TO BLOB("PrivateKey.txt";$vbPrivateKey)
If(OK=1)
` ...and the sender’s public key
ALERT("Please select the sender’s public key.")
$vhDocRef:=Open document("") `Public key to load
If(OK=1)
CLOSE DOCUMENT($vhDocRef)
DOCUMENT TO BLOB(Document;$vbPublicKey)
`Decrypting the BLOB with two keys as parameters
DECRYPT BLOB($vbEncrypted;$vbPublicKey;$vbPrivateKey)
BLOB TO VARIABLE($vbEncrypted;$vtDecrypted)
CREATE RECORD([Private])
[Private]Info:=$vtDecrypted
SAVE RECORD([Private])
End if
End if
End if
Product: 4D
Theme: BLOB
Number:
689
Created: 4D v6.7
DECRYPT BLOB
GENERATE ENCRYPTION KEYPAIR
Encryption, Public Key, Private key, PKCS, Optimization
4D Language Reference ( 4D v11 SQL Release 6)
4D Language Reference ( 4D v12.4)
4D Language Reference ( 4D v14 R2)
4D Language Reference ( 4D v14 R3)
4D Language Reference ( 4D v13.5)
4D Language Reference ( 4D v14.3)
4D Language Reference ( 4D v14 R4)







